What is IP Spoofing?
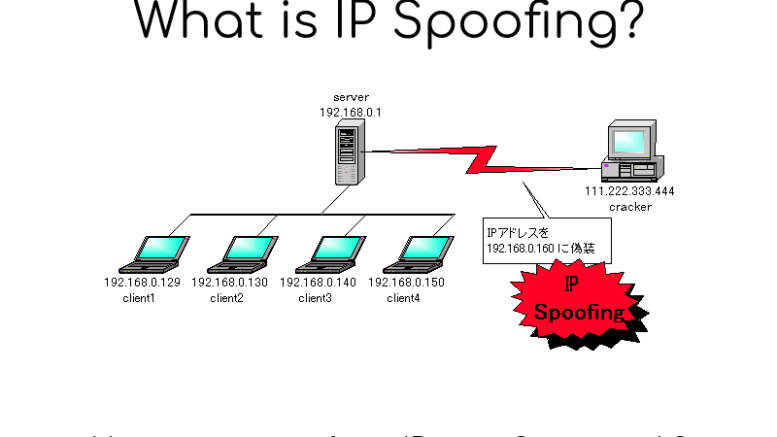
One can hide the sender’s identity and imitate a different computer, or both, by generating IP packets with a new source address. DDoS assaults on a target device or the surrounding infrastructure are launched using this method by bad actors. Packets of the Internet Protocol (IP) are the most common way for networked computers and other devices to interact. A header in every IP packet provides crucial routing information, including the source address, before the packet’s content. If you own an Asus Router, chances are you must have heard about port forwarding. For more information, visit our website for a comprehensive guide that makes it easy for you to start port forwarding on your Asus Router. Normally, the sender’s IP address is used as the source IP address in a packet. Forged source address indicates that the packet has been faked.
Spoofing is similar to an intruder who sends out packages that have an incorrect recipient’s address listed on them (for example). People who wish to restrict packages from being sent can ban all packets from a fictitious address, but that won’t help much because the address can readily be altered. Like the return address issue, if the recipient desires a reply, their response package will travel somewhere other than their original sender. An important weakness exploited by DDoS attacks is the ability to fake packet addresses.
Intending to overload the target with traffic while disguising the malicious source, DDoS assaults typically include spoofs. Falsified source IP addresses that are randomly generated make blocking fraudulent queries harder. Law enforcement and cyber security professionals are also hindered by IP spoofing to find out who is behind the assault. Using spoofing, a device may be impersonated by another, causing replies to be delivered to the target device instead of the original. Attacks that amplify NTP and DNS traffic make use of this flaw. TCP/architecture IPs include changing the source IP, making it a security risk. Spoofing is a technique that may be used in conjunction with DDoS assaults to bypass authentication and “hijack” a user’s session.
How does IP Spoofing Work?
The attacker changes the IP source address in outgoing packet headers to make it look like they’re coming from another IP address. It is done so that a destination computer will treat the packet as though it came from a trusted source (such as a computer). The target machine will accept it on the corporate network. As a result, regular users cannot utilize IP addresses used by hackers to send packets to malicious services. There can be hundreds of machines in a large BOTNET, each of which can block several source IP addresses at once. These automated attacks are therefore difficult to detect.
Most Common IP Spoofing Tools In 2021:
-
Caller ID Spoofing
Spoofing is the process of tricking a telephone network into telling a caller’s receiver that they are receiving a call from someone else. This can cause the caller ID display to reflect a different phone number than the one used to call. Commonly, the phrase is used to describe instances when the creator believes the motivation is nefarious.
Because of the broad availability of Caller ID spoofing, “you can no longer trust caller ID,” according to an AARP report from 2019. A specific type of digital connection to the telephone company known as an ISDN-PRI circuit allows users to fake their caller ID for years. The tactic has been employed by collection agencies, law enforcement authorities, and private detectives, with various degrees of legality. Star38.com, a California-based company, introduced the first widespread caller ID spoofing service in the United States on September 1, 2004. Jason Jepson created the first service that allowed users to conduct faked calls through a web interface. In 2005, it ceased to operate due to the introduction of a number of similar sites. To get access to a voicemail system that relied on the caller ID for verification, Paris Hilton was accused in August 2006. For example, on Craigslist and eBay, caller ID spoofing is utilized in purchasing frauds.

The scammer is phoning from Canada to the United States with a genuine interest in acquiring offered products. A copy of a registered title or other personal information is often requested from the vendors before a (scammer) purchaser makes the trip to inspect the sale items. Fake caller IDs of ambulance firms and hospitals were used in the 2010 Missouri election to entice potential voters to pick up the phone and vote for the Democratic candidate. In 2009, an angry Brooklyn wife impersonated her husband’s mistress’s physician to mislead her into taking a medicine that would cause her to miscarry.
Spoofing caller ID is frequently employed in prank calls. When a buddy answers the phone, “The White House” appears on the caller display. The unknown hacker sent the SWAT squad to the residence of the unknowing victim in December 2007 by using caller-ID spoofing service. A guy in Collegeville, Pennsylvania, made threatening phone calls to ladies. His home number appeared on their caller ID, giving the impression that the call originated from inside their home. Unwanted telemarketers began presenting the victim’s phone numbers in 2014, either verbatim or randomized, to avoid caller ID-based blacklists.
-
Email Address Spoofing
This technique involves sending emails using a fake sender address. Due to the lack of built-in authentication techniques in email’s initial transmission protocols, spam and phishing emails can use spoofing to deceive the recipient. As a result of more recent countermeasures, it has become harder but not impossible to spoof emails from internet sources; few internal networks have defenses against emails impersonating from an infected machine on the web. It has been proven that email spoofing has resulted in severe corporate and financial losses. In October 2013, an international news agency received a phony Fingerprint Cards email. Samsung had made an offer to purchase the company. Stock prices soared by 50% as a result of the dissemination of the news. Email addresses are regularly scanned by modern spyware such as Klez or Sober. They utilize such addresses to send emails and construct convincing faked From fields in the emails they send. This will increase the likelihood of the emails being opened. Using an example:
- A malicious email is sent to Alice, which she opens and executes the worm code.
- For example, the worm code looks for Bob and Charlie’s email addresses in Alice’s email address book in the instance of Alice.
- It then forges an email that appears to have been sent by Charlie but was sent by Alice’s computer.
For example, even if Bob’s system detects the incoming mail as malicious, he still perceives the message’s sender as Charlie, even if it originated from Alice’s computer. Alice can stay uninformed, and Charlie can be unaware until he receives an error notice from Bob.
-
GPS Spoofing
By broadcasting false GPS signals or by rebroadcasting actual signals collected at another location or at a different time in an attempt to fool a GPS receiver, the attacker tries to deceive the GPS receiver.
Depending on the attacker, these faked signals may induce the receiver to believe that it is situated somewhere other than where it is or located where it truly is, but at a different time. Some GPS attacks, known as “carry-off” attacks, begin by transmitting signals synced with those detected by receivers at their targets. It is thus possible to progressively raise the power of the counterfeit signs, thereby removing them from the real signals.
Reads More: Mini Chainsaw Suitable for Woodcarving Tools
A strike of this kind may have resulted in the seizure of a Lockheed RQ-170 drone aircraft in December 2011 in northern Iran. However, there has yet to be a verified malicious spoofing assault. Students from the Cockrell School of Engineering of the University of Texas successfully faked GPS signals on the luxury yacht, White Rose of Drachs, in June 2013, as part of a “proof-of-concept” assault. Students were on board after enabling their spoofing technology to overcome the GPS constellation satellites progressively, causing the boat to veer off course.
-
Voice Spoofing
Vocal biometrics is one of the authentication methods used to restrict access to informational resources in today’s society due to the rising importance given to information technology. An Internet banking system, a contact center’s system for verifying client identity, and even the police’s “blacklist” system are all examples of systems that use speech recognition. Due to rapid and fast-paced advancements in technology, it is now possible for you to make voice recordings that are virtually indistinguishable from those made by humans. In this context, TTS or Style Transfer Services are used. In the first, the goal was to create a new individual. Identifies another person in speech recognition systems.
To do this, a significant number of scientists are working on algorithmic methods for distinguishing between synthetic and genuine voices. These algorithms must be carefully evaluated before being used in production to ensure that the system is working.
How Can You Defend Yourself Against IP Spoofing?
A few examples of measures to take to avoid IP spoofing include:
- Encrypt all communication to and from your server using secure encryption methods (SEC). Make sure to always see “HTTPS” in the URL bar of websites you visit, along with the padlock symbol.
- If you get an email asking you to update your password, credit card information, or make a gift, delete it immediately. While the coronavirus epidemic was going on, hackers were making a lot of money via phishing emails. A few fake emails claim the newest COVID-19 information, while others seek to cash in return as a contribution. They may appear to be from legitimate companies, but in reality, they were sent by fraudsters. Enter the website URL straight into your browser instead of clicking on the link provided by those phishing emails. This will prevent you from being tricked.
- You may also make efforts to make visiting the web more secure. The same goes for using a public Wi-Fi network, which isn’t safe. It would be best to utilize a virtual private network (VPN) to secure your data when using public hotspots.
- Security software that includes a VPN might be beneficial. Incoming communication will be scanned by antivirus software to guarantee that no malware infiltrates the system. It’s critical to maintain your software up to date. Updating your software guarantees that it is equipped with the most recent encryption, authentication, and security fixes.
- To help safeguard your network, set up a firewall that filters faked IP traffic, verifies that traffic, and blocks access by unwanted outsiders. As a result, IP addresses may be verified.
- Protect your Wi-Fi network at home by using a strong password and a strong encryption key. A strong password mixes capital and lowercase letters, a symbol, and a numeric character. As a secondary form of protection, choose long passwords that you can remember but are difficult for others to guess.
- Keep an eye on unusual behavior on your network.
- A computer networking method called ingress filters can guarantee that packets arriving from trusted sources and not from hackers are filtered. Packet source header analysis is used for this. Outbound traffic may be monitored using egress filtering and packets that do not have authentic source headers or conform to security requirements.

Be the first to comment on "Most Common IP Spoofing Tools In 2021"